Table of Contents
The dark web is the World Wide Web content that exists on darknets (overlay networks) that use the Internet, but require specific software, configurations, or authorization to access. Through the dark web, private computer networks can communicate and conduct business anonymously without divulging identifying information, such as a user’s location.The dark web forms a small part of the deep web, the part of the web not indexed by web search engines, although sometimes the term deep web is mistakenly used to refer specifically to the dark web.
The darknets which constitute the dark web include small, friend-to-friend networks, as well as large, popular networks such as Tor, Hyphanet, I2P, and Riffle operated by public organizations and individuals. Users of the dark web refer to the regular web as clearnet due to its unencrypted nature. The Tor dark web or onionland uses the traffic anonymization technique of onion routing under the network’s top-level domain suffix .onion.

What is Dark Web?
The dark web has often been confused with the deep web, the parts of the web not indexed (searchable) by search engines. The term dark web first emerged in 2009; however, it is unknown when the actual dark web first emerged. Many internet users only use the surface web, data that can be accessed by a typical web browser. The dark web forms a small part of the deep web, but requires custom software in order to access its content. This confusion dates back to at least 2009. Since then, especially in reporting on Silk Road, the two terms have often been conflated, despite recommendations that they should be distinguished.
The dark web, also known as darknet websites, are accessible only through networks such as Tor (“The Onion Routing” project) that are created specifically for the dark web. Tor browser and Tor-accessible sites are widely used among the darknet users and can be identified by the domain “.onion”. Tor browsers create encrypted entry points and pathways for the user, allowing their dark web searches and actions to be anonymous.
Identities and locations of darknet users stay anonymous and cannot be tracked due to the layered encryption system. The darknet encryption technology routes users’ data through a large number of intermediate servers, which protects the users’ identity and guarantees anonymity. The transmitted information can be decrypted only by a subsequent node in the scheme, which leads to the exit node. The complicated system makes it almost impossible to reproduce the node path and decrypt the information layer by layer.Due to the high level of encryption, websites are not able to track geolocation and IP of their users, and users are not able to get this information about the host. Thus, communication between darknet users is highly encrypted allowing users to talk, blog, and share files confidentially.

Dark Web Reality
Dark Web is a studio album by American producer Keith Rankin, known by his stage name Giant Claw, released in September 2014 worldwide by the labels Orange Milk Records, Noumenal Loom, and in Japan by Virgin Babylon. Dark Web depicts the idea of existing cultures and music coming together to form, in the words of Orange Milk, “new compositional tools.” As such, its melodies are executed from a combination of half-second-length snippets of vocal samples from pop and R&B songs. Dark Web follows Giant Claw’s typical style of samples and MIDI compositions but with more influences of modern music than Rankin’s previous records. Dark Web garnered a favorable critical response for its odd tone and landed in the year-end lists of publications such as Tiny Mix Tapes and CMJ.
As with other works by Giant Claw, Dark Web employs a mixture of samples and originally-composed, complex MIDI riffs. The album follows a concept about hyperrealism, the idea of parts of existing cultures and records being used to combine together “new compositional tools,” as the press release by Orange Milk Records puts it. The album is meant to portray “late night browsing sessions gone wrong, when YouTube clips and SoundCloud links and iTunes tracks melt together in an amalgam of cultural signposts and musical signifiers,” stated Fact magazine. Dark Web is based on the idea of humans unknowingly becoming parts of bigger trends than their actual “individual instincts.” As Dummy magazine analyzed, “It’s hard to tell what’s authentic and what’s appropriated on ‘Dark Web’: it’s both strikingly unique, yet made of familiar sounds.”
Rankin produced Dark Web based on three factors, what he described as the “layers of reality.” The first layer was the primary compositional elements, “things people are used to picking up on instantly,” including rhythm, melody, harmonic structure, and timbre. The second factor is the signals of the culture or time period affiliation of the samples.The album’s vocals are sampled from 1990s R&B and pop, and, as Rankin stated, the time of the source material is indicated by the “extra-musical layer” of the “tiny affectations in the original vocals.”
How he edited and processed the samples is the third layer, and he intended to make this the clearest one to the listener: “my creative intention was to make the listener subconsciously realize that the historical sample was being manipulated, that the culture is being used as a new compositional tool.”For every track, Rankin first gathered the vocal stems for Dark Web before cutting less than half of a second from all of them to combine and perform original riffs. He added, “The takeaway from that is that the sample doesn’t matter, whether you’re sampling or composing something yourself. The end result is the significant statement. I think that goes against a lot of reactions to sampling itself that I’ve seen in the past few years: “it’s not music, it’s not original because it’s been sampled,” and so on.”

Red Room Dark Web
Red rooms can be thought of as video gateways. They are also hidden pages where the visitor can see a person being tortured live (streaming) and even contribute to the torture by making suggestions or requests for the person being tortured. It’s a site that broadcasts live violent, sexual, and other ‘bad’ videos for the amusement of others over the Tor hidden network (deep web). The red room would have looked like if the film wasn’t a film and the girl was being tortured against her will while it was streamed anonymously on the dark web. Remember that women aren’t the focus of everything you read or hear. Some red rooms torment both men and animals.There are also many fakes and scams in the Deep Web Red Rooms. As a result of serious customers paying and being cheated, the general perception of red rooms is that they are all fraudulent.
Terrorists’ extensive use of the Dark Web puts our time and peace on the line. This is because terrorists have discovered new methods of hiding from law enforcement agencies, making it easier for them to carry out their plots. Because of this, terrorists have a significant edge over law enforcement because they cannot be tracked or identified through online behavior. Many more people are becoming radicalized and influenced by terrorists. Governments and law enforcement agencies often cannot spring on terrorists after learning of their communications and whereabouts because of the encrypted messaging provided by the Dark Web and other end-to-end encrypted apps like Telegram or WhatsApp. This is a major issue because we won’t know what terrorists will do next. The Dark Web makes it easier for terrorists and their backers to fund their operations as far as attack preparations go. Terrorists don’t give a damn if their financial transactions go through; they gain greater influence by getting donations from people who buy guns and ammunition.
Dark Web Marketplace
A darknet market is a commercial website on the dark web that operates via darknets such as Tor and I2P. They function primarily as black markets, selling or brokering transactions involving drugs, cyber-arms, weapons, counterfeit currency, stolen credit card details, forged documents, unlicensed pharmaceuticals, steroids, and other illicit goods as well as the sale of legal products. In December 2014, a study by Gareth Owen from the University of Portsmouth suggested the second most popular sites on Tor were darknet markets.
Following on from the model developed by Silk Road, contemporary markets are characterized by their use of darknet anonymized access (typically Tor), Bitcoin or Monero payment with escrow services, and eBay-like vendor feedback systems.
The first marketplace to use both Tor and Bitcoin escrow was Silk Road, founded by Ross Ulbricht under pseudonym “Dread Pirate Roberts” in February 2011. In June 2011, Gawker published an article about the site, which led to “Internet buzz” and an increase in website traffic. This in turn led to political pressure from Senator Chuck Schumer on the US DEA and Department of Justice to shut it down, which they finally did in October 2013 after a lengthy investigation.Silk Road’s use of all of Tor, Bitcoin escrow and feedback systems would set the standard for new darknet markets for the coming years. The shutdown was described by news site DeepDotWeb as “the best advertising the dark net markets could have hoped for” following the proliferation of competing sites this caused, and The Guardian predicted others would take over the market that Silk Road previously dominated.
Atlantis, the first site to accept Litecoin as well as Bitcoin, closed in September 2013, just prior to the Silk Road raid, leaving users just one week to withdraw any coins. In October 2013, Project Black Flag closed and stole their users’ bitcoins in the panic shortly after Silk Road’s shut down. Black Market Reloaded’s popularity increased dramatically after the closure of Silk Road and Sheep Marketplace; however, in late November 2013, the owner of Black Market Reloaded announced that the website would be taken offline due to the unmanageable influx of new customers this caused. Sheep Marketplace, which launched in March 2013, was one of the lesser known sites to gain popularity with Silk Road’s closure. Not long after those events, in December 2013, it ceased operation after two Florida men stole $6 million worth of users’ Bitcoins.

The underground economy is known as the new and growing trend in dark market transactions. In 2015, the Federal Bureau of Investigation seized $34.5 million after raiding a well-known deep web bazaar for drugs. Once a considerable amount of bitcoin (BTC) money has been moved to these marketplaces, it is common to shut down the site to prohibit outgoing transfers and take the money you’ve locked into it. Cryptocurrencies are bringing new types of economic crime organizations that are difficult to uncover using conventional police and financial/tax investigation techniques due to the main concern that they might be utilized to enable illicit transactions and services. According to some deep web specialists, the hitmen services marketed on the dark web are scams. However, many advertisements for assassinations and hitmen services appear to be scams. For the time being, there are just a few cryptocurrencies in use on the darknet markets that can be considered more reputable because of their rapid value and price gains in a relatively short period, such as BTC, Monero, and others. While multifunctional, decentralized, and less vulnerable systems are becoming increasingly popular in the darknet market, the blockchain technology that underpins cryptocurrencies is increasingly being extended into other business applications and platforms, bringing corporations together in production and commercial alliances.
What’s the Difference Between Deep Web and Dark Web?
Millions of regular internet users access private databases such as email inboxes and credit card accounts daily. These pages are not indexed by search engines and are protected behind security walls, authentication forms, and passwords on the deep web.
Approximately 90% of all websites are on the deep web, and many are used by entities such as corporations, government agencies, and nonprofits. What’s known as the dark web exists within the deep web; it’s an area of the internet that is only accessible by users who have a Tor browser installed. In general, most average internet users will never need to access content on the dark web, although it is perfectly legal to use Tor.
Legal Uses of Dark Web
While using the dark web may seem suspect on the surface, it is perfectly legal, and there are many legitimate uses of Tor and anonymous browsing. For example, in countries where government surveillance may be used to spy on and oppress political dissidents, the dark web is often a place for communication that avoids government censorship and scrutiny. Despite these added layers of security, users should still be cautious using the dark web and take proper security measures, such as periodically updating their security software, browsing with a robust VPN, and avoiding the use of a standard email address.
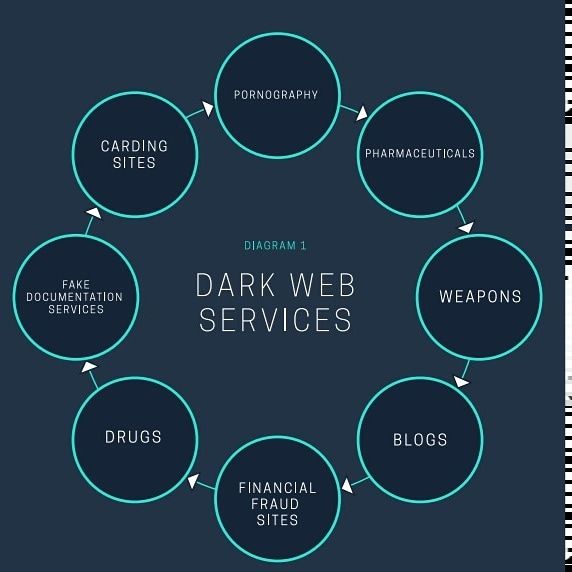
Illegal Uses of Dark Web
Given its anonymous nature, the dark web is also used for illicit and even illegal purposes. These include the buying and selling of illegal drugs, weapons, passwords, and stolen identities, as well as the trading of illegal pornography and other potentially harmful materials. Several sites hosting illegal material have been discovered by government agencies and shut down in recent years, including Silk Road, AlphaBay, and Hansa. The dark web’s anonymity has also led to cybersecurity threats and various data breaches over the last few decades.





